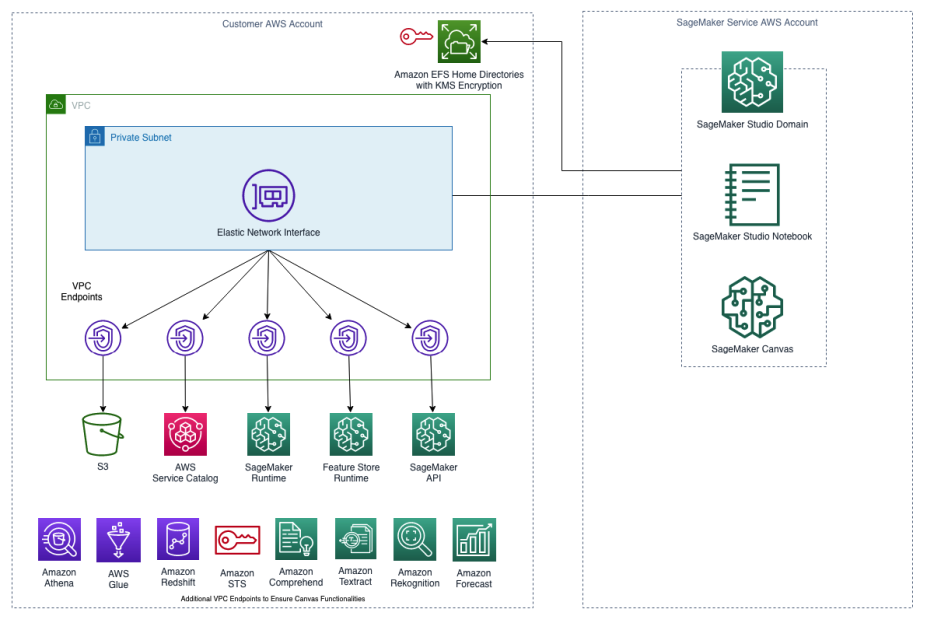
Amazon SageMaker Area in VPC solely mode to assist SageMaker Studio with auto shutdown Lifecycle Configuration and SageMaker Canvas with Terraform
Amazon SageMaker Domain helps SageMaker machine studying (ML) environments, together with SageMaker Studio and SageMaker Canvas. SageMaker Studio is a totally built-in growth setting (IDE) that gives a single web-based visible interface the place you’ll be able to entry purpose-built instruments to carry out all ML growth steps, from getting ready information to constructing, coaching, and deploying your ML fashions, bettering information science staff productiveness by as much as 10x. SageMaker Canvas expands entry to machine studying by offering enterprise analysts with a visible interface that permits them to generate correct ML predictions on their very own—with out requiring any ML expertise or having to jot down a single line of code.
HashiCorp Terraform is an infrastructure as code (IaC) device that allows you to arrange your infrastructure in reusable code modules. AWS clients depend on IaC to design, develop, and handle their cloud infrastructure, corresponding to SageMaker Domains. IaC ensures that buyer infrastructure and providers are constant, scalable, and reproducible whereas following finest practices within the space of growth operations (DevOps). Utilizing Terraform, you’ll be able to develop and handle your SageMaker Area and its supporting infrastructure in a constant and repeatable method.
On this submit, we exhibit the Terraform implementation to deploy a SageMaker Area and the Amazon Virtual Private Cloud (Amazon VPC) it associates with. The answer will use Terraform to create:
- A VPC with subnets, safety teams, in addition to VPC endpoints to assist VPC solely mode for the SageMaker Area.
- A SageMaker Area in VPC solely mode with a consumer profile.
- An AWS Key Administration Service (AWS KMS) key to encrypt the SageMaker Studio’s Amazon Elastic File System (Amazon EFS) quantity.
- A Lifecycle Configuration hooked up to the SageMaker Area to mechanically shut down idle Studio pocket book cases.
- A SageMaker Area execution position and IAM insurance policies to allow SageMaker Studio and Canvas functionalities.
The answer described on this submit is accessible at this GitHub repo.
Resolution overview
The next picture reveals SageMaker Area in VPC solely mode.
By launching SageMaker Area in your VPC, you’ll be able to management the info circulation out of your SageMaker Studio and Canvas environments. This lets you limit web entry, monitor and examine site visitors utilizing normal AWS networking and safety capabilities, and connect with different AWS assets via VPC endpoints.
VPC necessities to make use of VPC solely mode
Making a SageMaker Area in VPC solely mode requires a VPC with the next configurations:
- At the least two non-public subnets, every in a unique Availability Zone, to make sure excessive availability.
- Guarantee your subnets have the required variety of IP addresses wanted. We advocate between two and 4 IP addresses per consumer. The full IP tackle capability for a Studio area is the sum of obtainable IP addresses for every subnet supplied when the area is created.
- Arrange a number of safety teams with inbound and outbound guidelines that collectively enable the next site visitors:
- NFS site visitors over TCP on port 2049 between the area and the Amazon EFS quantity.
- TCP site visitors inside the safety group. That is required for connectivity between the JupyterServer app and the KernelGateway apps. You need to enable entry to not less than ports within the vary 8192–65535.
- Create a gateway endpoint for Amazon Easy Storage Service (Amazon S3). SageMaker Studio must entry Amazon S3 out of your VPC utilizing Gateway VPC endpoints. After you create the gateway endpoint, you want to add it as a goal in your route desk for site visitors destined out of your VPC to Amazon S3.
- Create interface VPC endpoints (AWS PrivateLink) to permit Studio to entry the next providers with the corresponding service names. You need to additionally affiliate a safety group on your VPC with these endpoints to permit all inbound site visitors from port 443:
- SageMaker API:
com.amazonaws.area.sagemaker.api. That is required to speak with the SageMaker API. - SageMaker runtime:
com.amazonaws.area.sagemaker.runtime. That is required to run Studio notebooks and to coach and host fashions. - SageMaker Characteristic Retailer:
com.amazonaws.area.sagemaker.featurestore-runtime. That is required to make use of SageMaker Characteristic Retailer. - SageMaker Tasks:
com.amazonaws.area.servicecatalog. That is required to make use of SageMaker Tasks.
- SageMaker API:
Extra VPC endpoints to make use of SageMaker Canvas
Along with the beforehand talked about VPC endpoints, to make use of SageMaker Canvas, you want to additionally create the next interface VPC endpoints:
- Amazon Forecast and Amazon Forecast Question:
com.amazonaws.area.forecastandcom.amazonaws.area.forecastquery. These are required to make use of Amazon Forecast. - Amazon Rekognition:
com.amazonaws.area.rekognition. That is required to make use of Amazon Rekognition. - Amazon Textract:
com.amazonaws.area.textract. That is required to make use of Amazon Textract. - Amazon Comprehend:
com.amazonaws.area.comprehend. That is required to make use of Amazon Comprehend. - AWS Safety Token Service (AWS STS):
com.amazonaws.area.sts. That is required as a result of SageMaker Canvas makes use of AWS STS to hook up with information sources. - Amazon Athena and AWS Glue:
com.amazonaws.area.athenaandcom.amazonaws.area.glue. That is required to hook up with AWS Glue Knowledge Catalog via Amazon Athena. - Amazon Redshift:
com.amazonaws.area.redshift-data. That is required to hook up with the Amazon Redshift information supply.
To view all VPC endpoints for every service you should use with SageMaker Canvas, please go to Configure Amazon SageMaker Canvas in a VPC without internet access.
AWS KMS encryption for SageMaker Studio’s EFS quantity
The primary time a consumer in your staff onboards to SageMaker Studio, SageMaker creates an EFS quantity for the staff. A house listing is created within the quantity for every consumer who onboards to Studio as a part of your staff. Pocket book recordsdata and information recordsdata are saved in these directories.
You may encrypt your SageMaker Studio’s EFS quantity with a KMS key so your house directories’ information are encrypted at relaxation. This Terraform resolution creates a KMS key and makes use of it to encrypt SageMaker Studio’s EFS quantity.
SageMaker Area Lifecycle Configuration to mechanically shut down idle Studio notebooks
Lifecycle Configurations are shell scripts triggered by Amazon SageMaker Studio lifecycle occasions, corresponding to beginning a brand new Studio pocket book. You should utilize Lifecycle Configurations to automate customization on your Studio setting.
This Terraform resolution creates a SageMaker Lifecycle Configuration to detect and cease idle assets that incur prices inside Studio utilizing an auto-shutdown Jupyter extension. Beneath the hood, the next assets are created or configured to realize the specified end result:
- Create an S3 bucket and add the most recent model of the auto-shutdown extension
sagemaker_studio_autoshutdown-0.1.5.tar.gz. Later, the auto-shutdown script will run thes3 cpcommand to obtain the extension file from the S3 bucket on Jupyter Server start-ups. Please consult with the next GitHub repos for extra data relating to the auto-shutdown extension and auto-shutdown script. - Create an aws_sagemaker_studio_lifecycle_config useful resource “
auto_shutdown”. This useful resource will encode theautoshutdown-script.shwith base 64 and create a Lifecycle Configuration for the SageMaker Area. - For SageMaker Area default consumer settings, specify the Lifecycle Configuration arn and set it as default.
SageMaker execution position IAM permissions
As a managed service, SageMaker performs operations in your behalf on the AWS {hardware} that’s managed by SageMaker. SageMaker can carry out solely operations that the consumer permits.
A SageMaker consumer can grant these permissions with an IAM position (known as an execution position). If you create a SageMaker Studio area, SageMaker lets you create the execution position by default. You may limit entry to consumer profiles by altering the SageMaker consumer profile position. This Terraform resolution attaches the next IAM insurance policies to the SageMaker execution position:
- SageMaker managed
AmazonSageMakerFullAccesscoverage. This coverage grants the execution position full entry to make use of SageMaker Studio. - A buyer managed IAM coverage to entry the KMS key used to encrypt the SageMaker Studio’s EFS quantity.
- SageMaker managed
AmazonSageMakerCanvasFullAccessandAmazonSageMakerCanvasAIServicesAccessinsurance policies. These insurance policies grant the execution position full entry to make use of SageMaker Canvas. - So as to allow time collection evaluation in SageMaker Canvas, you additionally want so as to add the IAM belief coverage for Amazon Forecast.
Resolution walkthrough
On this weblog submit, we exhibit deploy the Terraform resolution. Prior to creating the deployment, please guarantee to fulfill the next stipulations:
Conditions
- An AWS account
- An IAM consumer with administrative entry
Deployment steps
To present customers following this information a unified deployment expertise, we exhibit the deployment course of with AWS CloudShell. Utilizing CloudShell, a browser-based shell, you’ll be able to rapidly run scripts with the AWS Command Line Interface (AWS CLI), experiment with service APIs utilizing the AWS CLI, and use different instruments to extend your productiveness.
To deploy the Terraform resolution, full the next steps:
CloudShell launch settings
- Register to the AWS Administration Console and choose the CloudShell service.
- Within the navigation bar, within the Area selector, select US East (N. Virginia).
Your browser will open the CloudShell terminal.
Set up Terraform
The subsequent steps must be executed in a CloudShell terminal.
Test this Hashicorp guide for up-to-date directions to put in Terraform for Amazon Linux:
- Set up
yum-config-managerto handle your repositories.
- Use
yum-config-managerso as to add the official HashiCorp Linux repository.
- Set up Terraform from the brand new repository.
- Confirm that the set up labored by itemizing Terraform’s obtainable subcommands.
Anticipated output:
Clone the code repo
Carry out the next steps in a CloudShell terminal.
- Clone the repo and navigate to the sagemaker-domain-vpconly-canvas-with-terraform folder:
- Obtain the auto-shutdown extension and place it within the
belongings/auto_shutdown_templatefolder:
Deploy the Terraform resolution
Within the CloudShell terminal, run the next Terraform instructions:
You must see a hit message like:
Now you’ll be able to run:
After you might be glad with the assets the plan outlines to be created, you’ll be able to run:
Enter “sure“ when prompted to substantiate the deployment.
If efficiently deployed, it’s best to see an output that appears like:
Accessing SageMaker Studio and Canvas
We now have a Studio area related to our VPC and a consumer profile on this area.
To make use of the SageMaker Studio console, on the Studio Management Panel, find your consumer title (it must be defaultuser) and select Open Studio.
We made it! Now you should use your browser to hook up with the SageMaker Studio setting. After a couple of minutes, Studio finishes creating your setting, and also you’re greeted with the launcher display.
To make use of the SageMaker Canvas console, on the Canvas Management Panel, find your consumer title (must be defaultuser) and select Open Canvas.
Now you should use your browser to hook up with the SageMaker Canvas setting. After a couple of minutes, Canvas finishes creating your setting, and also you’re greeted with the launcher display.
Be at liberty to discover the complete performance SageMaker Studio and Canvas has to supply! Please consult with the Conclusion part for added workshops and tutorials you should use to be taught extra about SageMaker.
Clear up
Run the next command to scrub up your assets:
Tip: Should you set the Amazon EFS retention coverage as “Retain” (the default), you’ll run into points throughout “terraform destroy” as a result of Terraform is attempting to delete the subnets and VPC when the EFS quantity in addition to its related safety teams (created by SageMaker) nonetheless exist. To repair this, first delete the EFS quantity manually after which delete the subnets and VPC manually within the AWS console.
Conclusion
The answer on this submit offers you the power to create a SageMaker Area to assist ML environments, together with SageMaker Studio and SageMaker Canvas with Terraform. SageMaker Studio offers a totally managed IDE that removes the heavy lifting within the ML course of. With SageMaker Canvas, our enterprise customers can simply discover and construct ML fashions to make correct predictions with out writing any code. With the power to launch Studio and Canvas inside a VPC and the usage of a KMS key to encrypt the EFS quantity, clients can use SageMaker ML environments with enhanced safety. Auto shutdown Lifecycle Configuration helps clients save prices on idle Studio pocket book cases.
Go check this resolution and tell us what you assume. For extra details about use SageMaker Studio and Sagemaker Canvas, see the next:
Concerning the Creator
 Chen Yang is a Machine Studying Engineer at Amazon Net Providers. She is a part of the AWS Skilled Providers staff, and has been specializing in constructing safe machine studying environments for patrons. In her spare time, she enjoys operating and mountain climbing within the Pacific Northwest.
Chen Yang is a Machine Studying Engineer at Amazon Net Providers. She is a part of the AWS Skilled Providers staff, and has been specializing in constructing safe machine studying environments for patrons. In her spare time, she enjoys operating and mountain climbing within the Pacific Northwest.