Onboard customers to Amazon SageMaker Studio with Lively Listing group-specific IAM roles
Amazon SageMaker Studio is a web-based built-in growth atmosphere (IDE) for machine studying (ML) that permits you to construct, prepare, debug, deploy, and monitor your ML fashions. For provisioning Studio in your AWS account and Area, you first must create an Amazon SageMaker area—a assemble that encapsulates your ML atmosphere. Extra concretely, a SageMaker area consists of an related Amazon Elastic File System (Amazon EFS) quantity, a listing of licensed customers, and quite a lot of safety, utility, coverage, and Amazon Virtual Private Cloud (Amazon VPC) configurations.
When creating your SageMaker area, you’ll be able to select to make use of both AWS IAM Identity Center (successor to AWS Single Signal-On) or AWS Identity and Access Management (IAM) for person authentication strategies. Each authentication strategies have their very own set of use instances; on this submit, we deal with SageMaker domains with IAM Identification Middle, or single sign-on (SSO) mode, because the authentication methodology.
With SSO mode, you arrange an SSO person and group in IAM Identification Middle after which grant entry to both the SSO group or person from the Studio console. Presently, all SSO customers in a website inherit the area’s execution function. This will not work for all organizations. For example, directors might need to arrange IAM permissions for a Studio SSO person based mostly on their Lively Listing (AD) group membership. Moreover, as a result of directors are required to manually grant SSO customers entry to Studio, the method might not scale when onboarding tons of of customers.
On this submit, we offer prescriptive steerage for the answer to provision SSO customers to Studio with least privilege permissions based mostly on AD group membership. This steerage allows you to shortly scale for onboarding tons of of customers to Studio and obtain your safety and compliance posture.
Resolution overview
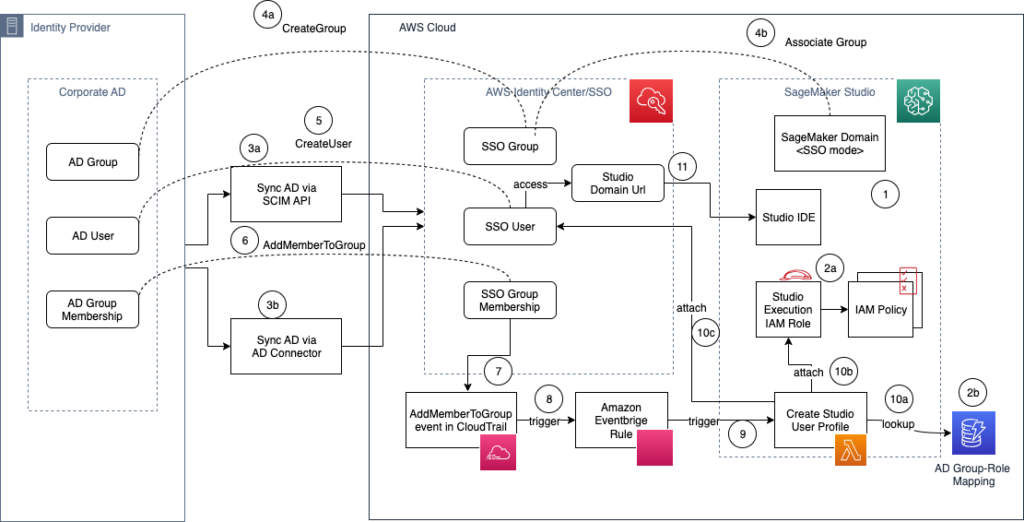
The next diagram illustrates the answer structure.

The workflow to provision AD customers in Studio contains the next steps:
- Arrange a Studio domain in SSO mode.
- For every AD group:
- Arrange your Studio execution function with acceptable fine-grained IAM insurance policies
- Document an entry within the AD group-role mapping Amazon DynamoDB desk.
Alternatively, you’ll be able to undertake a naming customary for IAM function ARNs based mostly on the AD group identify and derive the IAM function ARN without having to retailer the mapping in an exterior database.
- Sync your AD customers and teams and memberships to AWS Identification Middle:
- In the event you’re utilizing an identification supplier (IdP) that helps SCIM, use the SCIM API integration with IAM Identification Middle.
- In case you are utilizing self-managed AD, you could use AD Connector.
- When the AD group is created in your company AD, full the next steps:
- Create a corresponding SSO group in IAM Identification Middle.
- Affiliate the SSO group to the Studio area utilizing the SageMaker console.
- When an AD person is created in your company AD, a corresponding SSO person is created in IAM Identification Middle.
- When the AD person is assigned to an AD group, an IAM Identification Middle API (CreateGroupMembership) is invoked, and SSO group membership is created.
- The previous occasion is logged in AWS CloudTrail with the identify
AddMemberToGroup. - An Amazon EventBridge rule listens to CloudTrail occasions and matches the
AddMemberToGrouprule sample. - The EventBridge rule triggers the goal AWS Lambda perform.
- This Lambda perform will name again IAM Identification Middle APIs, get the SSO person and group info, and carry out the next steps to create the Studio person profile (CreateUserProfile) for the SSO person:
- Lookup the DynamoDB desk to fetch the IAM function similar to the AD group.
- Create a person profile with the SSO person and the IAM function obtained from the lookup desk.
- The SSO person is granted entry to Studio.
- The SSO person is redirected to the Studio IDE by way of the Studio area URL.
Word that, as of writing, Step 4b (affiliate the SSO group to the Studio area) must be carried out manually by an admin utilizing the SageMaker console on the SageMaker area stage.
Arrange a Lambda perform to create the person profiles
The answer makes use of a Lambda perform to create the Studio person profiles. We offer the next pattern Lambda perform you can copy and modify to satisfy your wants for automating the creation of the Studio person profile. This perform performs the next actions:
- Obtain the CloudTrail
AddMemberToGroupoccasion from EventBridge. - Retrieve the Studio
DOMAIN_IDfrom the atmosphere variable (you’ll be able to alternatively hard-code the area ID or use a DynamoDB desk as nicely if in case you have a number of domains). - Learn from a dummy markup desk to match AD customers to execution roles. You may change this to fetch from the DynamoDB desk should you’re utilizing a table-driven strategy. In the event you use DynamoDB, your Lambda perform’s execution function wants permissions to learn from the desk as nicely.
- Retrieve the SSO person and AD group membership info from IAM Identification Middle, based mostly on the CloudTrail occasion knowledge.
- Create a Studio person profile for the SSO person, with the SSO particulars and the matching execution function.
Word that by default, the Lambda execution function doesn’t have entry to create person profiles or checklist SSO customers. After you create the Lambda perform, entry the perform’s execution function on IAM and connect the next coverage as an inline coverage after scoping down as wanted based mostly in your group necessities.
Arrange the EventBridge rule for the CloudTrail occasion
EventBridge is a serverless occasion bus service that you should use to attach your purposes with knowledge from quite a lot of sources. On this answer, we create a rule-based set off: EventBridge listens to occasions and matches towards the offered sample and triggers a Lambda perform if the sample match is profitable. As defined within the answer overview, we hearken to the AddMemberToGroup occasion. To set it up, full the next steps:
- On the EventBridge console, select Guidelines within the navigation pane.
- Select Create rule.
- Present a rule identify, for instance,
AddUserToADGroup. - Optionally, enter an outline.
- Choose default for the occasion bus.
- Below Rule sort, select Rule with an occasion sample, then select Subsequent.
- On the Construct occasion sample web page, select Occasion supply as AWS occasions or EventBridge companion occasions.
- Below Occasion sample, select the Customized patterns (JSON editor) tab and enter the next sample:
- Select Subsequent.
- On the Choose goal(s) web page, select the AWS service for the goal sort, the Lambda perform because the goal, and the perform you created earlier, then select Subsequent.
- Select Subsequent on the Configure tags web page, then select Create rule on the Evaluate and create web page.
After you’ve set the Lambda perform and the EventBridge rule, you’ll be able to take a look at out this answer. To take action, open your IdP and add a person to one of many AD teams with the Studio execution function mapped. When you add the person, you’ll be able to confirm the Lambda perform logs to examine the occasion and likewise see the Studio person provisioned robotically. Moreover, you should use the DescribeUserProfile API name to confirm that the person is created with acceptable permissions.
Supporting a number of Studio accounts
To help a number of Studio accounts with the previous structure, we advocate the next modifications:
- Arrange an AD group mapped to every Studio account stage.
- Arrange a group-level IAM function in every Studio account.
- Arrange or derive the group to IAM function mapping.
- Arrange a Lambda perform to carry out cross-account role assumption, based mostly on the IAM function mapping ARN and created person profile.
Deprovisioning customers
When a person is faraway from their AD group, it’s best to take away their entry from the Studio area as nicely. With SSO, when a person is eliminated, the person is disabled in IAM Identification Middle robotically if the AD to IAM Identification Middle sync is in place, and their Studio utility entry is straight away revoked.
Nonetheless, the person profile on Studio nonetheless persists. You may add an identical workflow with CloudTrail and a Lambda perform to take away the person profile from Studio. The EventBridge set off ought to now hear for the DeleteGroupMembership occasion. Within the Lambda perform, full the next steps:
- Get hold of the person profile identify from the person and group ID.
- Listing all working apps for the person profile utilizing the ListApps API name, filtering by the
UserProfileNameEqualsparameter. Be sure to test for the paginated response, to checklist all apps for the person. - Delete all working apps for the person and wait till all apps are deleted. You should utilize the DescribeApp API to view the app’s standing.
- When all apps are in a Deleted state (or Failed), delete the person profile.
With this answer in place, ML platform directors can preserve group memberships in a single central location and automate the Studio person profile administration by way of EventBridge and Lambda features.
The next code reveals a pattern CloudTrail occasion:
The next code reveals a pattern Studio person profile API request:
Conclusion
On this submit, we mentioned how directors can scale Studio onboarding for tons of of customers based mostly on their AD group membership. We demonstrated an end-to-end answer structure that organizations can undertake to automate and scale their onboarding course of to satisfy their agility, safety, and compliance wants. In the event you’re on the lookout for a scalable answer to automate your person onboarding, do that answer, and depart you suggestions under! For extra details about onboarding to Studio, see Onboard to Amazon SageMaker Domain.
In regards to the authors
 Ram Vittal is an ML Specialist Options Architect at AWS. He has over 20 years of expertise architecting and constructing distributed, hybrid, and cloud purposes. He’s captivated with constructing safe and scalable AI/ML and massive knowledge options to assist enterprise clients with their cloud adoption and optimization journey to enhance their enterprise outcomes. In his spare time, he rides his bike and walks along with his 2-year-old sheep-a-doodle!
Ram Vittal is an ML Specialist Options Architect at AWS. He has over 20 years of expertise architecting and constructing distributed, hybrid, and cloud purposes. He’s captivated with constructing safe and scalable AI/ML and massive knowledge options to assist enterprise clients with their cloud adoption and optimization journey to enhance their enterprise outcomes. In his spare time, he rides his bike and walks along with his 2-year-old sheep-a-doodle!
 Durga Sury is an ML Options Architect within the Amazon SageMaker Service SA staff. She is captivated with making machine studying accessible to everybody. In her 4 years at AWS, she has helped arrange AI/ML platforms for enterprise clients. When she isn’t working, she loves bike rides, thriller novels, and mountain climbing along with her 5-year-old husky.
Durga Sury is an ML Options Architect within the Amazon SageMaker Service SA staff. She is captivated with making machine studying accessible to everybody. In her 4 years at AWS, she has helped arrange AI/ML platforms for enterprise clients. When she isn’t working, she loves bike rides, thriller novels, and mountain climbing along with her 5-year-old husky.





