Giant language mannequin inference over confidential knowledge utilizing AWS Nitro Enclaves
This publish is co-written with Justin Miles, Liv d’Aliberti, and Joe Kovba from Leidos.
Leidos is a Fortune 500 science and know-how options chief working to handle among the world’s hardest challenges within the protection, intelligence, homeland safety, civil, and healthcare markets. On this publish, we talk about how Leidos labored with AWS to develop an method to privacy-preserving massive language mannequin (LLM) inference utilizing AWS Nitro Enclaves.
LLMs are designed to know and generate human-like language, and are utilized in many industries, together with authorities, healthcare, monetary, and mental property. LLMs have broad applicability, together with chatbots, content material technology, language translation, sentiment evaluation, query answering methods, serps, and code technology. Introducing LLM-based inference right into a system additionally has the potential to introduce privateness threats, together with mannequin exfiltration, knowledge privateness violations, and unintended LLM-based service manipulation. Technical architectures must be applied with a view to make it possible for LLMs don’t expose delicate info throughout inference.
This publish discusses how Nitro Enclaves can assist shield LLM mannequin deployments, particularly people who use personally identifiable info (PII) or protected well being info (PHI). This publish is for instructional functions solely and shouldn’t be utilized in manufacturing environments with out further controls.
Overview of LLMs and Nitro Enclaves
A possible use case is an LLM-based delicate question chatbot designed to hold out a query and answering service containing PII and PHI. Most present LLM chatbot options explicitly inform customers that they need to not embrace PII or PHI when inputting questions on account of safety issues. To mitigate these issues and shield buyer knowledge, service house owners rely totally on person protections similar to the next:
- Redaction – The method of figuring out and obscuring delicate info like PII in paperwork, texts, or different types of content material. This may be completed with enter knowledge earlier than being despatched to a mannequin or an LLM educated to redact their responses mechanically.
- Multi-factor authentication – A safety course of that requires customers to offer a number of authentication strategies to confirm their id to realize entry to the LLM.
- Transport Layer Safety (TLS) – A cryptographic protocol that gives safe communication that enhances knowledge privateness in transit between customers and the LLM service.
Though these practices improve the safety posture of the service, they aren’t enough to safeguard all delicate person info and different delicate info that may persist with out the person’s information.
In our instance use case, an LLM service is designed to reply worker healthcare profit questions or present a private retirement plan. Let’s analyze the next pattern structure and determine knowledge privateness danger areas.
The potential danger areas are as follows:
- Privileged customers have entry to the occasion that homes the server. Unintentional or unauthorized modifications to the service may lead to delicate knowledge being uncovered in unintended methods.
- Customers should belief the service won’t expose or retain delicate info in software logs.
- Modifications to software packages may cause modifications to the service, ensuing within the publicity of delicate knowledge.
- Privileged customers with entry to the occasion have unrestricted entry to the LLM utilized by the service. Modifications might trigger incorrect or inaccurate info being returned to customers.
Nitro Enclaves offers further isolation to your Amazon Elastic Compute Cloud (Amazon EC2) occasion, safeguarding knowledge in use from unauthorized entry, together with admin-level customers. Within the previous structure, it’s doable for an unintentional change to lead to delicate knowledge to persist in plaintext and by accident get revealed to a person who might not must entry that knowledge. With Nitro Enclaves, you create an remoted surroundings out of your EC2 occasion, allowing you to allocate CPU and reminiscence sources to the enclave. This enclave is a extremely restrictive digital machine. By working code that handles delicate knowledge throughout the enclave, not one of the guardian’s processes will have the ability to view enclave knowledge.
Nitro Enclaves gives the next advantages:
- Reminiscence and CPU Isolation – It depends on the Nitro Hypervisor to isolate the CPU and reminiscence of the enclave from customers, functions, and libraries on the guardian occasion. This characteristic helps isolate the enclave and your software program, and considerably reduces the floor space for unintended occasions.
- Separate digital machine – Enclaves are separated digital machines connected to an EC2 occasion to additional shield and securely course of extremely delicate knowledge.
- No interactive entry – Enclaves present solely safe native socket connectivity with their guardian occasion. They don’t have any persistent storage, interactive entry, or exterior networking.
- Cryptographic attestation – Nitro Enclaves gives cryptographic attestation, a course of used to show the id of an enclave and confirm that solely licensed code is working in your enclave.
- AWS integration – Nitro Enclaves is built-in with AWS Key Management Service (AWS KMS), permitting you to decrypt recordsdata which have been encrypted utilizing AWS KMS contained in the enclave. AWS Certificate Manager (ACM) for Nitro Enclaves means that you can use private and non-private SSL/TLS certificates along with your net functions and servers working on EC2 cases with Nitro Enclaves.
You need to use these options supplied by Nitro Enclaves to assist mitigate dangers related to PII and PHI knowledge. We suggest together with Nitro Enclaves in an LLM service when dealing with delicate person knowledge.
Answer overview
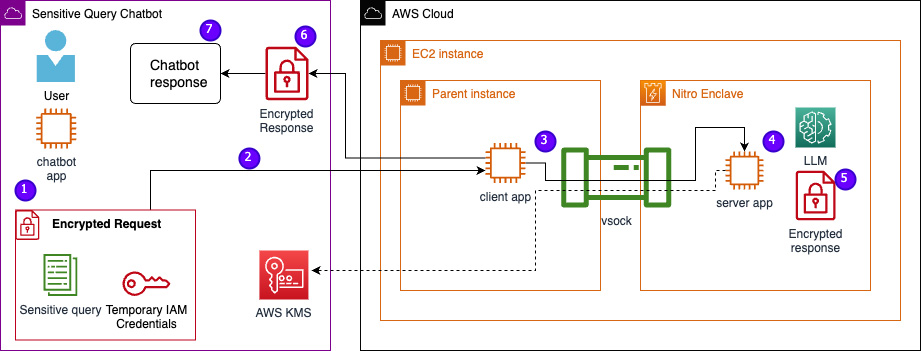
Let’s study the structure of the instance service, now together with Nitro Enclaves. By incorporating Nitro Enclaves, as proven within the following determine, the LLM turns into a safer chatbot for dealing with PHI or PII knowledge.
Consumer knowledge, together with PII, PHI, and questions, stays encrypted all through the request-response course of when the applying is hosted inside an enclave. The steps carried out through the inference are as follows:
- The chatbot app generates non permanent AWS credentials and asks the person to enter a query. The query, which can comprise PII or PHI, is then encrypted by way of AWS KMS. The encrypted person enter is mixed with the non permanent credentials to create the encrypted request.
- The encrypted knowledge is distributed to an HTTP server hosted by Flask as a POST request. Earlier than accepting delicate knowledge, this endpoint ought to be configured for HTTPs.
- The consumer app receives the POST request and forwards it by a safe native channel (for instance, vsock) to the server app working inside Nitro Enclaves.
- The Nitro Enclaves server app makes use of the non permanent credentials to decrypt the request, queries the LLM, and generates the response. The model-specific settings are saved throughout the enclaves and are protected with cryptographic attestation.
- The server app makes use of the identical non permanent credentials to encrypt the response.
- The encrypted response is returned again to the chatbot app by the consumer app as a response from the POST request.
- The chatbot app decrypts the response utilizing their KMS key and shows the plaintext to the person.
Conditions
Earlier than we get began, you want the next stipulations to deploy the answer:
Configure an EC2 occasion
Full the next steps to configure an EC2 occasion:
- Launch an r5.8xlarge EC2 occasion utilizing the amzn2-ami-kernel-5.10-hvm-2.0.20230628.0-x86_64-gp2 AMI with Nitro Enclaves enabled.
- Set up the Nitro Enclaves CLI to construct and run Nitro Enclaves functions:
sudo amazon-linux-extras set up aws-nitro-enclaves-cli -ysudo yum set up aws-nitro-enclaves-cli-devel -y
- Confirm the set up of the Nitro Enclaves CLI:
nitro-cli –model- The model used on this publish is 1.2.2
- Set up Git and Docker to construct Docker pictures and obtain the applying from GitHub. Add your occasion person to the Docker group (<USER> is your IAM occasion person):
sudo yum set up git -ysudo usermod -aG ne <USER>sudo usermod -aG docker <USER>sudo systemctl begin docker && sudo systemctl allow docker
- Begin and allow the Nitro Enclaves allocator and vsock proxy providers:
sudo systemctl begin nitro-enclaves-allocator.service && sudo systemctl allow nitro-enclaves-allocator.servicesudo systemctl begin nitro-enclaves-vsock-proxy.service && sudo systemctl allow nitro-enclaves-vsock-proxy.service
Nitro Enclaves makes use of a neighborhood socket connection known as vsock to create a safe channel between the guardian occasion and the enclave.
After all of the providers are began and enabled, restart the occasion to confirm that the entire person teams and providers are working accurately:
sudo shutdown -r now
Configure the Nitro Enclaves allocator service
Nitro Enclaves is an remoted surroundings that designates a portion of the occasion CPU and reminiscence to run the enclave. With the Nitro Enclaves allocator service, you’ll be able to point out what number of CPUs and the way a lot reminiscence will probably be taken from the guardian occasion to run the enclave.
Modify the enclave’s reserved sources utilizing a textual content editor (for our answer, we allocate 8 CPU and 70,000 MiB reminiscence to offer sufficient sources):
vi /and so forth/nitro_enclaves/allocatory.yaml
Clone the challenge
After you configure the EC2 occasion, you’ll be able to obtain the code to run the delicate chatbot with an LLM within Nitro Enclaves.
You might want to replace the server.py file with the suitable KMS key ID that you simply created at first to encrypt the LLM response.
- Clone the GitHub challenge:
cd ~/ && git clone https://<THE_REPO.git>
- Navigate to the challenge folder to construct the
enclave_baseDocker picture that comprises the Nitro Enclaves Software Development Kit (SDK) for cryptographic attestation paperwork from the Nitro Hypervisor (this step can take as much as quarter-hour):cd /nitro_llm/enclave_basedocker construct ./ -t “enclave_base”
Save the LLM within the EC2 Occasion
We’re utilizing the open-source Bloom 560m LLM for pure language processing to generate responses. This mannequin just isn’t fine-tuned to PII and PHI, however demonstrates how an LLM can stay within an enclave. The mannequin additionally must be saved on the guardian occasion in order that it may be copied into the enclave by way of the Dockerfile.
- Navigate to the challenge:
- Set up the mandatory necessities to save lots of the mannequin regionally:
pip3 set up necessities.txt
- Run the
save_model.pyapp to save lots of the mannequin throughout the/nitro_llm/enclave/bloomlisting:
Construct and run the Nitro Enclaves picture
To run Nitro Enclaves, you could create an enclave picture file (EIF) from a Docker picture of your software. The Dockerfile situated within the enclave listing comprises the recordsdata, code, and LLM that may run within the enclave.
Constructing and working the enclave will take a number of minutes to finish.
- Navigate to the foundation of the challenge:
- Construct the enclave picture file as
enclave.eif:nitro-cli build-enclave --docker-uri enclave:newest --output-file enclave.eif
When the enclave is constructed, a collection of distinctive hashes and platform configuration registers (PCRs) will probably be created. The PCRs are a contiguous measurement to show the id of the {hardware} and software. These PCRs will probably be required for cryptographic attestation and used through the KMS key coverage replace step.
- Run the enclave with the sources from the
allocator.service(including the--attach-consoleargument on the finish will run the enclave in debug mode):nitro-cli run-enclave --cpu-count 8 --memory 70000 --enclave-cid 16 --eif-path enclave.eif
You might want to allocate at the very least 4 instances the EIF file dimension. This may be modified within the allocator.service from earlier steps.
- Confirm the enclave is working with the next command:
nitro-cli describe-enclaves
Replace the KMS key coverage
Full the next steps to replace your KMS key coverage:
- On the AWS KMS console, select Buyer managed keys within the navigation pane.
- Seek for the important thing that you simply generated as a prerequisite.
- Select Edit on the important thing coverage.
- Replace the important thing coverage with the next info:
- Your account ID
- Your IAM person identify
- The up to date Cloud9 surroundings occasion function
- Actions
kms:Encryptandkms:Decrypt - Enclave PCRs (for instance, PCR0, PCR1, PCR2) to your key coverage with a situation assertion
See the next key coverage code:
Save the chatbot app
To imitate a delicate question chatbot software that lives outdoors of the AWS account, you could save the chatbot.py app and run it contained in the Cloud9 surroundings. Your Cloud9 surroundings will use its occasion function for non permanent credentials to disassociate permissions from the EC2 working the enclave. Full the next steps:
- On the Cloud9 console, open the surroundings you created.
- Copy the next code into a brand new file like
chatbot.pyinto the principle listing. - Set up the required modules:
pip set up boto3Pip set up requests
- On the Amazon EC2 console, word the IP related along with your Nitro Enclaves occasion.
- Replace the URL variable in
http://<ec2instanceIP>:5001.
- Run the chatbot software:
When it’s working, the terminal will ask for the person enter and comply with the architectural diagram from earlier to generate a safe response.
Run the non-public query and reply chatbot
Now that Nitro Enclaves is up and working on the EC2 occasion, you’ll be able to extra securely ask your chatbot PHI and PII questions. Let’s have a look at an instance.
Throughout the Cloud9 surroundings, we ask our chatbot a query and supply our person identify.
AWS KMS encrypts the query, which seems to be like the next screenshot.
It’s then despatched to the enclave and requested of the secured LLM. The query and response of the LLM will appear like the next screenshot (the consequence and encrypted response are seen contained in the enclave solely in debug mode).
The result’s then encrypted utilizing AWS KMS and returned to the Cloud9 surroundings to be decrypted.
Clear up
Full the next steps to wash up your sources:
- Cease the EC2 occasion created to accommodate your enclave.
- Delete the Cloud9 surroundings.
- Delete the KMS key.
- Take away the EC2 occasion function and IAM person permissions.
Conclusion
On this publish, we showcased find out how to use Nitro Enclaves to deploy an LLM query and answering service that extra securely sends and receives PII and PHI info. This was deployed on Amazon EC2, and the enclaves are built-in with AWS KMS proscribing entry to a KMS key, so solely Nitro Enclaves and the end-user are allowed to make use of the important thing and decrypt the query.
Should you’re planning to scale this structure to assist bigger workloads, ensure the mannequin choice course of matches your mannequin necessities with EC2 sources. Moreover, you could take into account the utmost request dimension and what impression that may have on the HTTP server and inference time towards the mannequin. Many of those parameters are customizable by the mannequin and HTTP server settings.
One of the best ways to find out the particular settings and necessities to your workload is thru testing with a fine-tuned LLM. Though this publish solely included pure language processing of delicate knowledge, you’ll be able to modify this structure to assist alternate LLMs supporting audio, pc imaginative and prescient, or multi-modalities. The identical safety rules highlighted right here will be utilized to knowledge in any format. The sources used to construct this publish can be found on the GitHub repo.
Share how you’ll adapt this answer to your surroundings within the feedback part.
Concerning the Authors
Justin Miles is a cloud engineer throughout the Leidos Digital Modernization Sector underneath the Workplace of Expertise. In his spare time, he enjoys {golfing} and touring.
Liv d’Aliberti is a researcher throughout the Leidos AI/ML Accelerator underneath the Workplace of Expertise. Their analysis focuses on privacy-preserving machine studying.
Chris Renzo is a Sr. Answer Architect throughout the AWS Protection and Aerospace group. Outdoors of labor, he enjoys a steadiness of heat climate and touring.
Joe Kovba is a Vice President throughout the Leidos Digital Modernization Sector. In his free time, he enjoys refereeing soccer video games and enjoying softball.













