Construct personal and safe enterprise generative AI purposes with Amazon Q Enterprise utilizing IAM Federation

Amazon Q Business is a conversational assistant powered by generative artificial intelligence (AI) that enhances workforce productiveness by answering questions and finishing duties based mostly on info in your enterprise techniques, which every person is permitted to entry. In an earlier submit, we mentioned how you can build private and secure enterprise generative AI applications with Amazon Q Business and AWS IAM Identity Center. If you wish to use Amazon Q Enterprise to construct enterprise generative AI purposes, and have but to undertake organization-wide use of AWS IAM Identity Center, you need to use Amazon Q Business IAM Federation to immediately handle person entry to Amazon Q Enterprise purposes out of your enterprise id supplier (IdP), equivalent to Okta or Ping Id. Amazon Q Enterprise IAM Federation makes use of Federation with IAM and doesn’t require using IAM Id Heart.
AWS recommends utilizing AWS Id Heart if in case you have numerous customers so as to obtain a seamless person entry administration expertise for a number of Amazon Q Enterprise purposes throughout many AWS accounts in AWS Organizations. You should use federated teams to outline entry management, and a person is charged just one time for his or her highest tier of Amazon Q Enterprise subscription. Though Amazon Q Enterprise IAM Federation lets you construct personal and safe generative AI purposes, with out requiring using IAM Id Heart, it’s comparatively constrained with no assist for federated teams, and limits the flexibility to cost a person just one time for his or her highest tier of Amazon Q Enterprise subscription to Amazon Q Enterprise purposes sharing SAML id supplier or OIDC id supplier in a single AWS accouGnt.
This submit reveals how you need to use Amazon Q Enterprise IAM Federation for person entry administration of your Amazon Q Enterprise purposes.
Answer overview
To implement this answer, you create an IAM identity provider for SAML or IAM identity provider for OIDC based mostly in your IdP software integration. When creating an Amazon Q Enterprise software, you select and configure the corresponding IAM id supplier.
When responding to requests by an authenticated person, the Amazon Q Enterprise software makes use of the IAM id supplier configuration to validate the person id. The appliance can reply securely and confidentially by implementing entry management lists (ACLs) to generate responses from solely the enterprise content material the person is permitted to entry.
We use the identical instance from Build private and secure enterprise generative AI apps with Amazon Q Business and AWS IAM Identity Center—a generative AI worker assistant constructed with Amazon Q Enterprise—to exhibit set it up utilizing IAM Federation to solely reply utilizing enterprise content material that every worker has permissions to entry. Thus, the workers are in a position to converse securely and privately with this assistant.
Structure
Amazon Q Enterprise IAM Federation requires federating the person identities provisioned in your enterprise IdP equivalent to Okta or Ping Id account utilizing Federation with IAM. This entails a onetime setup of making a SAML or OIDC software integration in your IdP account, after which making a corresponding SAML identity provider or an OIDC identity provider in AWS IAM. This SAML or OIDC IAM id supplier is required so that you can create an Amazon Q Enterprise software. The IAM id supplier is utilized by the Amazon Q Enterprise software to validate and belief federated identities of customers authenticated by the enterprise IdP, and affiliate a singular id with every person. Thus, a person is uniquely recognized throughout all Amazon Q Enterprise purposes sharing the identical SAML IAM id supplier or OIDC IAM id supplier.
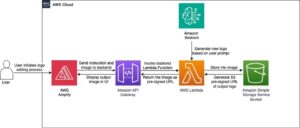
The next diagram reveals a high-level structure and authentication workflow. The enterprise IdP, equivalent to Okta or Ping Id, is used because the entry supervisor for an authenticated person to work together with an Amazon Q Enterprise software utilizing an Amazon Q internet expertise or a customized software utilizing an API.

The person authentication workflow consists of the next steps:
- The consumer software makes an authentication request to the IdP on behalf of the person.
- The IdP responds with id or entry tokens in OIDC mode, or a SAML assertion in SAML 2.0 mode. Amazon Q Enterprise IAM Federation requires the enterprise IdP software integration to offer a particular principal tag e mail attribute with its worth set to the e-mail tackle of the authenticated person. If person attributes equivalent to position or location (metropolis, state, nation) are current within the SAML or OIDC assertions, Amazon Q Enterprise will extract these attributes for personalization. These attributes are included within the id token claims in OIDC mode, and SAML assertions within the SAML 2.0 mode.
- The consumer software makes an AssumeRoleWithWebIdentity (OIDC mode) or AssumeRoleWithSAML (SAML mode) API name to AWS Security Token Service (AWS STS) to accumulate AWS Sig V4 credentials. Electronic mail and different attributes are extracted and enforced by the Amazon Q Enterprise software utilizing session tags in AWS STS. The AWS Sig V4 credentials embrace details about the federated person.
- The consumer software makes use of the credentials obtained within the earlier step to make Amazon Q Enterprise API calls on behalf of the authenticated person. The Amazon Q Enterprise software is aware of the person id based mostly on the credential used to make the API calls, reveals solely the particular person’s dialog historical past, and enforces doc ACLs. The appliance retrieves solely these paperwork from the index that the person is permitted to entry and are related to the person’s question, to be included as context when the question is shipped to the underlying giant language mannequin (LLM). The appliance generates a response based mostly solely on enterprise content material that the person is permitted to entry.
How subscriptions work with Amazon Q Enterprise IAM Federation
The way in which person subscriptions are dealt with once you use IAM Id Heart vs. IAM Federation is completely different.
For purposes that use IAM Id Heart, AWS will de-duplicate subscriptions throughout all Amazon Q Enterprise purposes accounts, and cost every person just one time for his or her highest subscription stage. De-duplication will apply provided that the Amazon Q Enterprise purposes share the identical group occasion of IAM Id Heart. Customers subscribed to Amazon Q Enterprise purposes utilizing IAM federation can be charged one time after they share the identical SAML IAM id supplier or OIDC IAM id supplier. Amazon Q Enterprise purposes can share the identical SAML IAM id supplier or OIDC IAM id supplier provided that they’re in the identical AWS account. For instance, should you use Amazon Q Enterprise IAM Federation, and wish to make use of Amazon Q Enterprise purposes throughout 3 separate AWS accounts, every AWS account would require its personal SAML id supplier or OIDC id supplier to be created and used within the corresponding Amazon Q Enterprise purposes, and a person subscribed to those three Amazon Q Enterprise purposes can be charged thrice. In one other instance, if a person is subscribed to some Amazon Q Enterprise purposes that use IAM Id Heart and others that use IAM Federation, they are going to be charged one time throughout all IAM Id Heart purposes and one time per SAML IAM id supplier or OIDC IAM id supplier utilized by the Amazon Q Enterprise purposes utilizing IAM Federation.
For Amazon Q Enterprise purposes utilizing IAM Id Heart, the Amazon Q Enterprise administrator immediately assigns subscriptions for teams and customers on the Amazon Q Enterprise administration console. For an Amazon Q Enterprise software utilizing IAM federation, the administrator chooses the default subscription tier throughout software creation. When an authenticated person logs in utilizing both the Amazon Q Enterprise software internet expertise or a customized software utilizing the Amazon Q Enterprise API, that person is mechanically subscribed to the default tier.
Limitations
On the time of writing, Amazon Q Enterprise IAM Federation has the next limitations:
- Amazon Q Enterprise doesn’t assist OIDC for Google and Microsoft Entra ID.
- There is no such thing as a built-in mechanism to validate a person’s membership to federated teams outlined within the enterprise IdP. For those who’re utilizing ACLs in your information sources with teams federated from the enterprise IdP, you need to use the PutGroup API to outline the federated teams within the Amazon Q Enterprise person retailer. This manner, the Amazon Q Enterprise software can validate a person’s membership to the federated group and implement the ACLs accordingly. This limitation doesn’t apply to configurations the place teams utilized in ACLs are outlined domestically inside the information sources. For extra info, consult with Group mapping.
Pointers to selecting a person entry mechanism
The next desk summarizes the rules to think about when selecting a person entry mechanism.
| Federation Kind | AWS Account Kind | Amazon Q Enterprise Subscription Billing Scope | Supported Id Supply | Different Concerns |
| Federated with IAM Id Heart | A number of accounts managed by AWS Organizations | AWS group, assist for federated group-level subscriptions to Amazon Q Enterprise purposes | All identity sources supported by IAM Identity Center: IAM Id Heart listing, Lively Listing, and IdP | AWS recommends this selection if in case you have numerous customers and a number of purposes, with many federated teams used to outline entry management and permissions. |
| Federated with IAM utilizing OIDC IAM id supplier | Single, standalone account | All Amazon Q Enterprise purposes inside a single standalone AWS account sharing the identical OIDC IAM id supplier | IdP with OIDC software integration | This technique is extra easy to configure in comparison with a SAML 2.0 supplier. It’s additionally much less advanced to share IdP software integrations throughout Amazon Q Enterprise internet experiences and customized purposes utilizing Amazon Q Enterprise APIs. |
| Federated with IAM utilizing SAML IAM id supplier | Single, standalone account | All Amazon Q Enterprise purposes inside a single standalone AWS account sharing the identical SAML IAM id supplier | IdP with SAML 2.0 software integration | This technique is extra advanced to configure in comparison with OIDC, and requires a separate IdP software integration for every Amazon Q Enterprise internet expertise. Some sharing is feasible for customized purposes utilizing Amazon Q Enterprise APIs. |
Stipulations
To implement the pattern use case described on this submit, you want an Okta account. This submit covers workflows for each OIDC and SAML 2.0, so you may observe both one or each workflows based mostly in your curiosity. You might want to create software integrations for OIDC or SAML mode, after which configure the respective IAM id suppliers in your AWS account, which can be required to create and configure your Amazon Q Enterprise purposes. Although you utilize the identical Okta account and the identical AWS account to create two Amazon Q Enterprise purposes one utilizing an OIDC IAM id supplier, and the opposite utilizing SAML IAM id supplier, the identical person subscribed to each these Amazon Q Enterprise purposes can be charged twice, since they don’t share the underlying SAML or OIDC IAM id suppliers.
Create an Amazon Q Enterprise software with an OIDC IAM id supplier
To arrange an Amazon Q Enterprise software with an OIDC IAM id identifier, you first configure the Okta software integration utilizing OIDC. You then create an IAM id supplier for that OIDC app integration, and create an Amazon Q Enterprise software utilizing that OIDC IAM id supplier. Lastly, you replace the Okta software integration with the online expertise URIs of the newly created Amazon Q Enterprise software.
Create an Okta software integration with OIDC
Full the next steps to create your Okta software integration with OIDC:
- On the administration console of your Okta account, select Purposes, then Purposes within the navigation pane.
- Select Create App Integration.
- For Signal-in technique, choose OIDC.
- For Software kind, choose Net Software.
- Select Subsequent.

- Give your app integration a reputation.
- Choose Authorization Code and Refresh Token for Grant Kind.
- Verify that Refresh token habits is ready to Use persistent token.
- For Signal-in redirect URIs, present a placeholder worth equivalent to
https://instance.com/authorization-code/callback.
You replace this later with the online expertise URI of the Amazon Q Enterprise software you create.
- On the Assignments tab, assign entry to applicable customers inside your group to your Amazon Q Enterprise software.
On this step, you may choose all customers in your Okta group, or select choose teams, equivalent to Finance-Group if it’s outlined, or choose particular person customers.
- Select Save to save lots of the app integration.
Your app integration will look just like the next screenshots.
- Observe the values for Consumer ID and Consumer secret to make use of in subsequent steps.


- On the Signal on tab, select Edit subsequent to OpenID Join ID Token.
- For Issuer, notice the Okta URL.
- Select Cancel.

- Within the navigation pane, select Safety after which API.
- Below API, Authorization Servers, select default.
- On the Claims tab, select Add Declare.
- For Title, enter
https://aws.amazon.com/tags. - For Embody in token kind, choose ID Token.
- For Worth, enter
{"principal_tags": {"Electronic mail": {person.e mail}}}. - Select Create.
The declare will look just like the next screenshot. It’s a finest observe to make use of a customized authorization server. Nonetheless, as a result of that is an illustration, we use the default authorization server.

Arrange an IAM id supplier for OIDC
To arrange an IAM id supplier for OIDC, full the next steps:
- On the IAM console, select Id suppliers within the navigation pane.
- Select Add supplier.
- For Supplier kind, choose OpenID Join.
- For Supplier URL, enter the Okta URL you copied earlier, adopted by
/oauth2/default. - For Viewers, enter the consumer ID you copied earlier.
- Select Add supplier.

Create an Amazon Q Enterprise software with the OIDC IAM id supplier
Full the next steps to create an Amazon Q Enterprise software with the OIDC IdP:
- On the Amazon Q Enterprise console, select Create software.
- Give the applying a reputation.
- For Entry administration technique, choose AWS IAM Id supplier.
- For Select an Id supplier kind, choose OpenID Join (OIDC).
- For Choose Id Supplier, select the IdP you created.
- For Consumer ID, enter the consumer ID of the Okta software integration you copied earlier.
- Go away the remaining settings as default and select Create.

- Within the Choose retriever step, except you need to change the retriever kind or the index kind, select Subsequent.
- For now, choose Subsequent on the Join information sources We configure the information supply later.
On the Handle entry web page, in Default subscription settings, Subscription Tier of Q Enterprise Professional is chosen by default. Which means that when an authenticated person begins utilizing the Amazon Q Enterprise software, they may mechanically get subscribed as Amazon Q Enterprise Professional. The Amazon Q Enterprise administrator can change the subscription tier for a person at any time.
- In Net expertise settings uncheck Create internet expertise. Select Carried out.

- On the Amazon Q Enterprise Purposes web page, select the applying you simply created to view the main points.
- Within the Software Particulars web page, notice the Software ID.

- In a brand new tab of your internet browser open the administration console for AWS Secrets Manager. Select Retailer a brand new secret.
- For Select secret kind select Different kind of secret. For Key/worth pairs, enter client_secret as key and enter the consumer secret you copied from the Okta software integration as worth. Select Subsequent.

- For Configure secret give a Secret identify.
- For Configure rotation, except you need to make any modifications, settle for the defaults, and select Subsequent.
- For Evaluation, overview the key you simply saved, and select Retailer.
- On AWS Secrets and techniques Supervisor, Secrets and techniques web page select the key you simply created. Observe the Secret identify and Secret ARN.

- Observe the directions on IAM role for an Amazon Q web experience using IAM Federation to create Net expertise IAM position, and Secret Supervisor Function. You’ll require the Amazon Q Enterprise Software ID, Secret identify and Secret ARN you copied earlier.
- Open the Software Particulars on your Amazon Q Enterprise software. Select Edit.
- For Replace software, there isn’t a have to make modifications. Select Replace.
- For Replace retriever, there isn’t a have to make modifications. Select Subsequent.
- For Join information sources, there isn’t a have to make modifications. Select Subsequent.
- For Replace entry, choose Create internet expertise.
- For Service position identify choose the online expertise IAM position you created earlier.
- For AWS Secrets and techniques Supervisor secret, choose the key you saved earlier.
- For Net Expertise to make use of Secrets and techniques: Service position identify, choose the Secret Supervisor Function you created earlier.
- Select Replace.

- On the Amazon Q Enterprise Purposes web page, select the applying you simply up to date to view the main points.
- Observe the worth for Deployed URL.

Earlier than you need to use the online expertise to work together with the Amazon Q Enterprise software you simply created, it’s worthwhile to replace the Okta software integration with the redirect URL of the online expertise.
- Open the Okta administration console, then open the Okta software integration you created earlier.
- On the Normal tab, select Edit subsequent to Normal Settings.
- For Signal-in redirect URIs, substitute the placeholder
https://instance.com/with the worth for Deployed URL of your internet expertise. Be sure theauthorization-code/callbacksuffix is just not deleted. The complete URL ought to seem likehttps://your_deployed_url/authorization-code/callback. - Select Save.

Create an Amazon Q Enterprise software with a SAML 2.0 IAM id supplier
The method to arrange an Amazon Q Enterprise software with a SAML 2.0 IAM id supplier is just like creating an software utilizing OIDC. You first configure an Okta software integration utilizing SAML 2.0. You then create an IAM id supplier for that SAML 2.0 app integration, and create an Amazon Q Enterprise software utilizing the SAML 2.0 IAM id supplier. Lastly, you replace the Okta software integration with the online expertise URIs of the newly created Amazon Q Enterprise software.
Create an Okta software integration with SAML 2.0
Full the next steps to create your Okta software integration with SAML 2.0:
- On the administration console of your Okta account, select Purposes, then Purposes within the navigation pane.
- Select Create App Integration.
- For Signal-in technique, choose SAML 2.0.
- Select Subsequent.

- On the Normal Settings web page, enter an app identify and select Subsequent.
This may open the Create SAML Integration web page.
- For Single sign-on URL, enter a placeholder URL equivalent to
https://instance.com/samland deselect Use this for Recipient URL and Vacation spot URL. - For Recipient URL, enter
https://signin.aws.amazon.com/saml. - For Vacation spot URL, enter the placeholder
https://instance.com/saml. - For Viewers URL (SP Entity ID), enter
https://signin.aws.amazon.com/saml. - For Title ID format, select Persistent.
- Select Subsequent after which End.
The placeholder values of https://instance.com will have to be up to date with the deployment URL of the Amazon Q Enterprise internet expertise, which you create in subsequent steps.

- On the Signal On tab of the app integration you simply created, notice the worth for Metadata URL.

- Open the URL in your internet browser, and put it aside in your native pc.
The metadata can be required in subsequent steps.

Arrange an IAM id supplier for SAML 2.0
To arrange an IAM IdP for SAML 2.0, full the next steps:
- On the IAM console, select Id suppliers within the navigation pane.
- Select Add supplier.
- For Supplier kind, choose SAML.
- Enter a supplier identify.
- For Metadata doc, select Select file and add the metadata doc you saved earlier.
- Select Add supplier.

- From the checklist of id suppliers, select the id supplier you simply created.
- Observe the values for ARN, Issuer URL, and SSO service location to make use of in subsequent steps.

Create an Amazon Q Enterprise software with the SAML 2.0 IAM id supplier
Full the next steps to create an Amazon Q Enterprise software with the SAML 2.0 IAM id supplier:
- On the Amazon Q Enterprise console, select Create software.
- Give the applying a reputation.
- For Entry administration technique, choose AWS IAM Id supplier.
- For Select an Id supplier kind, choose SAML.
- For Choose Id Supplier, select the IdP you created.
- Go away the remaining settings as default and select Create.

- Within the Choose retriever step, except you need to change the retriever kind or the index kind, select Subsequent.
- For now, select Subsequent on the Join information sources We are going to configure the information supply later.
On the Handle entry web page, in Default subscription settings, Subscription Tier of Q Enterprise Professional is chosen by default. Which means that when an authenticated person begins utilizing the Amazon Q Enterprise software, they may mechanically get subscribed as Amazon Q Enterprise Professional. The Amazon Q Enterprise administrator can change the subscription tier for a person at any time.
- For Net expertise settings, uncheck Create internet expertise. Select Carried out.

- On the Amazon Q Enterprise Purposes web page, select the applying you simply created.
- Within the Software Particulars web page, notice the Software ID.

- Observe the directions on IAM role for an Amazon Q web experience using IAM Federation to create Net expertise IAM position. You’ll require the Amazon Q Enterprise Software ID you copied earlier.
- Open the Software Particulars on your Amazon Q Enterprise software. Select Edit.
- For Replace software, there isn’t a have to make modifications. Select Replace.
- For Replace retriever, there isn’t a have to make modifications. Select Subsequent.
- For Join information sources, there isn’t a have to make modifications. Select Subsequent.
- For Replace entry, choose Create internet expertise.
- For this submit, we proceed with the default setting.
- For Authentication URL, enter the worth for SSO service location that you just copied earlier.
- Select Replace.

- On the Amazon Q Enterprise Purposes web page, select the applying you simply up to date to view the main points.
- Observe the values for Deployed URL and Net expertise IAM position ARN to make use of in subsequent steps.

Earlier than you need to use the online expertise to work together with the Amazon Q Enterprise software you simply created, it’s worthwhile to replace the Okta software integration with the redirect URL of the online expertise.
- Open the Okta administration console, then open the Okta software integration you created earlier.
- On the Normal tab, select Edit subsequent to SAML Settings.
- For Single sign-on URL and Vacation spot URL, substitute the placeholder
https://instance.com/with the worth for Deployed URL of your internet expertise. Be sure the/samlsuffix isn’t deleted. - Select Save.

- On the Edit SAML Integration web page, within the Attribute Statements (elective) part, add attribute statements as listed within the following desk.
This step is just not elective and these attributes are utilized by the Amazon Q Enterprise software to find out the id of the person, so remember to affirm their correctness.
| Title | Title format | Worth |
https://aws.amazon.com/SAML/Attributes/PrincipalTag:Electronic mail |
Unspecified | person.e mail |
https://aws.amazon.com/SAML/Attributes/Function |
Unspecified | <Net expertise IAM position ARN>,<identity-provider-arn> |
https://aws.amazon.com/SAML/Attributes/RoleSessionName |
Unspecified | person.e mail |
For the worth of the https://aws.amazon.com/SAML/Attributes/Function attribute, it’s worthwhile to concatenate the online expertise IAM position ARN and IdP ARN you copied earlier with a comma between them, with out areas or another characters.

- Select Subsequent and End.
- On the Assignments tab, assign customers who can entry the app integration you simply created.
This step controls entry to applicable customers inside your group to your Amazon Q Enterprise software. On this step, you may allow self-service so that each one customers in your Okta group, or select choose teams, equivalent to Finance-Group if it’s outlined, or choose particular person customers.

Arrange the information supply
Whether or not you created the Amazon Q Enterprise software utilizing an OIDC IAM id supplier or SAML 2.0 IAM id supplier, the process to create an information supply stays the identical. For this submit, we arrange an information supply for Atlassian Confluence. The next steps present configure the information supply for the Confluence surroundings. For extra particulars on arrange a Confluence information supply, consult with Connecting Confluence (Cloud) to Amazon Q Business.
- On the Amazon Q Enterprise Software particulars web page, select Add information supply.

- On the Add information supply web page, select Confluence.

- For Information supply identify, enter a reputation.
- For Supply, choose Confluence Cloud and enter the Confluence URL.

- For Authentication, choose Fundamental authentication and enter the Secrets and techniques Supervisor secret.
- For IAM position, choose Create a brand new service position.
- Go away the remaining settings as default.

- For Sync scope, choose the suitable content material to sync.
- Below House and regex patterns, present the Confluence areas to be included.
- For Sync mode, choose Full sync.
- For Sync run schedule, select Run on demand.
- Select Add information supply.

- After the information supply creation is full, select Sync now to start out the information supply sync.

Wait till the sync is full earlier than logging in to the online expertise to start out querying.

Worker AI assistant use case
As an instance how one can construct a safe and personal generative AI assistant on your staff utilizing Amazon Q Enterprise purposes, let’s take a pattern use case of an worker AI assistant in an enterprise company. Two new staff, Mateo Jackson and Mary Main, have joined the corporate on two completely different tasks, and have completed their worker orientation. They’ve been given company laptops, and their accounts are provisioned within the company IdP. They’ve been informed to get assist from the worker AI assistant for any questions associated to their new crew member actions and their advantages.
The corporate makes use of Confluence to handle their enterprise content material. The pattern Amazon Q software used to run the eventualities for this submit is configured with an information supply utilizing the built-in connector for Confluence to index the enterprise Confluence areas utilized by staff. The instance makes use of three Confluence areas with the next permissions:
- HR House – All staff, together with Mateo and Mary
- AnyOrgApp Mission House – Staff assigned to the undertaking, together with Mateo
- ACME Mission House – Staff assigned to the undertaking, together with Mary
Let’s have a look at how Mateo and Mary expertise their worker AI assistant.
Each are supplied with the URL of the worker AI assistant internet expertise. They use the URL and sign up to the IdP from the browsers of their laptops. Mateo and Mary each need to find out about their new crew member actions and their fellow crew members. They ask the identical inquiries to the worker AI assistant however get completely different responses, as a result of every has entry to separate tasks. Within the following screenshots, the browser window on the left is for Mateo Jackson and the one on the proper is for Mary Main. Mateo will get details about the AnyOrgApp undertaking and Mary will get details about the ACME undertaking.

Mateo chooses Sources underneath the query about crew members to take a better have a look at the crew member info, and Mary chooses Sources underneath the query for the brand new crew member guidelines. The next screenshots present their up to date views.

Mateo and Mary need to discover out extra about the advantages their new job presents and the way the advantages are relevant to their private and household conditions.
The next screenshot reveals that Mary asks the worker AI assistant questions on her advantages and eligibility.

Mary may also consult with the supply paperwork.

The next screenshot reveals that Mateo asks the worker AI assistant completely different questions on his eligibility.

Mateo seems on the following supply paperwork.

Each Mary and Mateo first need to know their eligibility for advantages. However after that, they’ve completely different inquiries to ask. Regardless that the benefits-related paperwork are accessible by each Mary and Mateo, their conversations with the worker AI assistant are personal and private. The peace of mind that their dialog historical past is personal and may’t be seen by another person is crucial for the success of a generative AI worker productiveness assistant.
Clear up
For those who created a brand new Amazon Q Enterprise software to check out the mixing with IAM federation, and don’t plan to make use of it additional, you may unsubscribe, take away mechanically subscribed customers from the applying, and delete it in order that your AWS account doesn’t accumulate prices.
- To unsubscribe and take away customers, go to the applying particulars web page and select Handle subscriptions.

- Choose all of the customers, select Take away to take away subscriptions, and select Carried out.

- To delete the applying after eradicating the customers, return to the applying particulars web page and select Delete.

Conclusion
For enterprise generative AI assistants such because the one proven on this submit to achieve success, they have to respect entry management in addition to guarantee the privateness and confidentiality of each worker. Amazon Q Enterprise achieves this by integrating with IAM Id Heart or with IAM Federation to offer an answer that authenticates every person and validates the person id at every step to implement entry management together with privateness and confidentiality.
On this submit, we confirmed how Amazon Q Enterprise IAM Federation makes use of SAML 2.0 and OIDC IAM id suppliers to uniquely determine a person authenticated by the enterprise IdP, after which that person id is used to match up doc ACLs arrange within the information supply. At question time, Amazon Q Enterprise responds to a person question using solely these paperwork that the person is permitted to entry. This performance is just like that achieved by the mixing of Amazon Q Enterprise with IAM Id Heart we noticed in an earlier post. Moreover, we additionally offered the rules to think about when selecting a person entry mechanism.
To be taught extra, consult with Amazon Q Business, now generally available, helps boost workforce productivity with generative AI and the Amazon Q Business User Guide.
Concerning the authors
 Abhinav Jawadekar is a Principal Options Architect within the Amazon Q Enterprise service crew at AWS. Abhinav works with AWS prospects and companions to assist them construct generative AI options on AWS.
Abhinav Jawadekar is a Principal Options Architect within the Amazon Q Enterprise service crew at AWS. Abhinav works with AWS prospects and companions to assist them construct generative AI options on AWS.
 Venky Nagapudi is a Senior Supervisor of Product Administration for Q Enterprise, Amazon Comprehend and Amazon Translate. His focus areas on Q Enterprise embrace person id administration, and utilizing offline intelligence from paperwork to enhance Q Enterprise accuracy and helpfulness.
Venky Nagapudi is a Senior Supervisor of Product Administration for Q Enterprise, Amazon Comprehend and Amazon Translate. His focus areas on Q Enterprise embrace person id administration, and utilizing offline intelligence from paperwork to enhance Q Enterprise accuracy and helpfulness.