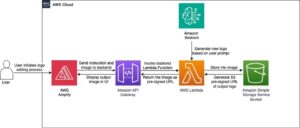
Use the ApplyGuardrail API with long-context inputs and streaming outputs in Amazon Bedrock

As generative artificial intelligence (AI) purposes change into extra prevalent, sustaining accountable AI ideas turns into important. With out correct safeguards, massive language fashions (LLMs) can doubtlessly generate dangerous, biased, or inappropriate content material, posing dangers to people and organizations. Making use of guardrails helps mitigate these dangers by implementing insurance policies and tips that align with moral ideas and authorized necessities. Guardrails for Amazon Bedrock evaluates person inputs and mannequin responses based mostly on use case-specific insurance policies, and supplies an extra layer of safeguards whatever the underlying basis mannequin (FM). Guardrails will be utilized throughout all LLMs on Amazon Bedrock, together with fine-tuned fashions and even generative AI purposes outdoors of Amazon Bedrock. You may create a number of guardrails, every configured with a distinct mixture of controls, and use these guardrails throughout completely different purposes and use instances. You may configure guardrails in multiple ways, together with to disclaim matters, filter dangerous content material, take away delicate info, and detect contextual grounding.
The brand new ApplyGuardrail API lets you assess any textual content utilizing your preconfigured guardrails in Amazon Bedrock, with out invoking the FMs. On this publish, we show use the ApplyGuardrail API with long-context inputs and streaming outputs.
ApplyGuardrail API overview
The ApplyGuardrail API affords a number of key options:
- Ease of use – You may combine the API anyplace in your utility movement to validate information earlier than processing or serving outcomes to customers. For instance, in a Retrieval Augmented Generation (RAG) utility, now you can consider the person enter previous to performing the retrieval as a substitute of ready till the ultimate response era.
- Decoupled from FMs – The API is decoupled from FMs, permitting you to make use of guardrails with out invoking FMs from Amazon Bedrock. For instance, now you can use the API with fashions hosted on Amazon SageMaker. Alternatively, you could possibly use it self-hosted or with fashions from third-party mannequin suppliers. All that’s wanted is taking the enter or output and request evaluation utilizing the API.
You should use the evaluation outcomes from the ApplyGuardrail API to design the expertise in your generative AI utility, ensuring it adheres to your outlined insurance policies and tips.
The ApplyGuardrail API request means that you can cross all of your content material that must be guarded utilizing your outlined guardrails. The supply area must be set to INPUT when the content material to evaluated is from a person, usually the LLM immediate. The supply must be set to OUTPUT when the mannequin output guardrails must be enforced, usually an LLM response. An instance request seems to be like the next code:
For extra details about the API construction, seek advice from Guardrails for Amazon Bedrock.
Streaming output
LLMs can generate textual content in a streaming method, the place the output is produced token by token or phrase by phrase, fairly than producing the complete output directly. This streaming output functionality is especially helpful in situations the place real-time interplay or steady era is required, resembling conversational AI assistants or reside captioning. Incrementally displaying the output permits for a extra pure and responsive person expertise. Though it’s advantageous by way of responsiveness, streaming output introduces challenges in relation to making use of guardrails in actual time because the output is generated. In contrast to the enter situation, the place the complete textual content is out there upfront, the output is generated incrementally, making it troublesome to evaluate the whole context and potential violations.
One of many fundamental challenges is the necessity to consider the output because it’s being generated, with out ready for the complete output to be full. This requires a mechanism to constantly monitor the streaming output and apply guardrails in actual time, whereas additionally contemplating the context and coherence of the generated textual content. Moreover, the choice to halt or proceed the era course of based mostly on the guardrail evaluation must be made in actual time, which may influence the responsiveness and person expertise of the applying.
Answer overview: Use guardrails on streaming output
To deal with the challenges of making use of guardrails on streaming output from LLMs, a method that mixes batching and real-time evaluation is required. This technique entails accumulating the streaming output into smaller batches or chunks, evaluating every batch utilizing the ApplyGuardrail API, after which taking acceptable actions based mostly on the evaluation outcomes.
Step one on this technique is to batch the streaming output chunks into smaller batches which are nearer to a text unit, which is roughly 1,000 characters. If a batch is smaller, resembling 600 characters, you’re nonetheless charged for a whole textual content unit (1,000 characters). For an economical utilization of the API, it’s advisable that the batches of chunks are so as of textual content models, resembling 1,000 characters, 2,000, and so forth. This manner, you decrease the danger of incurring pointless prices.
By batching the output into smaller batches, you may invoke the ApplyGuardrail API extra ceaselessly, permitting for real-time evaluation and decision-making. The batching course of must be designed to take care of the context and coherence of the generated textual content. This may be achieved by ensuring the batches don’t break up phrases or sentences, and by carrying over any crucial context from the earlier batch. Although the chunking varies between use instances, for the sake of simplicity, this publish showcases easy character-level chunking, but it surely’s advisable to discover choices resembling semantic chunking or hierarchical chunking whereas nonetheless adhering to the rules talked about on this publish.
After the streaming output has been batched into smaller chunks, every chunk will be handed to the API for analysis. The API will assess the content material of every chunk towards the outlined insurance policies and tips, figuring out any potential violations or delicate info.
The evaluation outcomes from the API can then be used to find out the suitable motion for the present batch. If a extreme violation is detected, the API evaluation suggests halting the era course of, and as a substitute a preset message or response will be exhibited to the person. Nevertheless, in some instances, no extreme violation is detected, however the guardrail was configured to cross by the request, for instance within the case of sensitiveInformationPolicyConfig to anonymize the detected entities as a substitute of blocking. If such an intervention happens, the output will likely be masked or modified accordingly earlier than being exhibited to the person. For latency-sensitive purposes, you can too take into account creating a number of buffers and a number of guardrails, every with completely different insurance policies, after which processing them with the ApplyGuardrail API in parallel. This manner, you may decrease the time it takes to make assessments for one guardrail at a time, however maximize getting the assessments from a number of guardrails and a number of batches, although this method hasn’t been applied on this instance.
Instance use case: Apply guardrails to streaming output
On this part, we offer an instance of how such a method may very well be applied. Let’s start with making a guardrail. You should use the next code sample to create a guardrail in Amazon Bedrock:
Correct evaluation of the insurance policies have to be performed to confirm if the enter must be later despatched to an LLM or whether or not the output generated by the LLM must be exhibited to the person. Within the following code, we look at the assessments, that are a part of the response from the ApplyGuardrail API, for potential extreme violation resulting in BLOCKED intervention by the guardrail:
We are able to then outline apply guardrail. If the response from the API results in an motion == 'GUARDRAIL_INTERVENED', it implies that the guardrail has detected a possible violation. We now must verify if the violation was extreme sufficient to dam the request or cross it by with both the identical textual content as enter or an alternate textual content during which modifications are made based on the outlined insurance policies:
Let’s now apply our technique for streaming output from an LLM. We are able to keep a buffer_text, which creates a batch of chunks obtained from the stream. As quickly as len(buffer_text + new_text) > TEXT_UNIT, which means if the batch is near a textual content unit (1,000 characters), it’s able to be despatched to the ApplyGuardrail API. With this mechanism, we will be certain we don’t incur the pointless price of invoking the API on smaller chunks and in addition that sufficient context is out there inside every batch for the guardrail to make significant assessments. Moreover, when the era is full from the LLM, the ultimate batch should even be examined for potential violations. If at any level the API detects extreme violations, additional consumption of the stream is halted and the person is displayed the preset message on the time of creation of the guardrail.
Within the following instance, we ask the LLM to generate three names and inform us what’s a financial institution. This era will result in GUARDRAIL_INTERVENED however not block the era, and as a substitute anonymize the textual content (masking the names) and proceed with era.
After working the previous code, we obtain an instance output with masked names:
Definitely! Listed here are three names of outstanding CEOs:
1. {NAME} - CEO of Apple Inc.
2. {NAME} - CEO of Microsoft Company
3. {NAME} - CEO of Amazon
Now, let's focus on what a financial institution is and the advantages of opening a financial savings account.
A financial institution is a monetary establishment that accepts deposits, supplies loans, and affords varied different monetary providers to its prospects. Banks play a vital function within the financial system by facilitating the movement of cash and enabling monetary transactions.
Lengthy-context inputs
RAG is a way that enhances LLMs by incorporating exterior data sources. It permits LLMs to reference authoritative data bases earlier than producing responses, producing output tailor-made to particular contexts whereas offering relevance, accuracy, and effectivity. The enter to the LLM in a RAG situation will be fairly lengthy, as a result of it contains the person’s question concatenated with the retrieved info from the data base. This long-context enter poses challenges when making use of guardrails, as a result of the enter could exceed the character limits imposed by the ApplyGuardrail API. To be taught extra concerning the quotas utilized to Guardrails for Amazon Bedrock, seek advice from Guardrails quotas.
We evaluated the technique to keep away from the danger from mannequin response within the earlier part. Within the case of inputs, the danger may very well be each on the question stage or along with the question and the retrieved context for the question.
The retrieved info from the data base could comprise delicate or doubtlessly dangerous content material, which must be recognized and dealt with appropriately, for instance masking sensitive information, earlier than being handed to the LLM for era. Subsequently, guardrails have to be utilized to the complete enter to ensure it adheres to the outlined insurance policies and constraints.
Answer overview: Use guardrails on long-context inputs
The ApplyGuardrail API has a default restrict of 25 text units (roughly 25,000 characters) per second. If the enter exceeds this restrict, it must be chunked and processed sequentially to keep away from throttling. Subsequently, the technique turns into comparatively simple: if the size of enter textual content is lower than 25 textual content models (25,000 characters), then it may be evaluated in a single request, in any other case it must be damaged down into smaller items. The chunk measurement can fluctuate relying on utility habits and the kind of context within the utility; you can begin with 12 textual content models and iterate to search out the very best appropriate chunk measurement. This manner, we maximize the allowed default restrict whereas retaining a lot of the context intact in a single request. Even when the guardrail motion is GUARDRAIL_INTERVENED, it doesn’t imply the enter is BLOCKED. It is also true that the enter is processed and delicate info is masked; on this case, the enter textual content have to be recompiled with any processed response from the utilized guardrail.
Run the full notebook to check this technique with long-context enter.
Finest practices and concerns
When making use of guardrails, it’s important to observe finest practices to take care of environment friendly and efficient content material moderation:
- Optimize chunking technique – Fastidiously take into account the chunking technique. The chunk measurement ought to steadiness the trade-off between minimizing the variety of API calls and ensuring the context isn’t misplaced as a result of overly small chunks. Equally, the chunking technique ought to bear in mind the context break up; a essential piece of textual content might span two (or extra) chunks if not fastidiously divided.
- Asynchronous processing – Implement asynchronous processing for RAG contexts. This will help decouple the guardrail utility course of from the primary utility movement, enhancing responsiveness and general efficiency. For ceaselessly retrieved context from vector databases,
ApplyGuardrailmay very well be utilized one time and outcomes saved in metadata. This might keep away from redundant API calls for a similar content material. This will considerably enhance efficiency and cut back prices. - Develop complete check suites – Create a complete check suite that covers a variety of situations, together with edge instances and nook instances, to validate the effectiveness of your guardrail implementation.
- Implement fallback mechanisms – There may very well be situations the place the guardrail created doesn’t cowl all of the attainable vulnerabilities and is unable to catch edge instances. For such situations, it’s sensible to have a fallback mechanism. One such possibility may very well be to convey human within the loop, or use an LLM as a decide to judge each the enter and output.
Along with the aforementioned concerns, it’s additionally good observe to often audit your guardrail implementation, constantly refine and adapt your guardrail implementation, and implement logging and monitoring mechanisms to seize and analyze the efficiency and effectiveness of your guardrails.
Clear up
The one useful resource we created on this instance is a guardrail. To delete the guardrail, full the next steps:
- On the Amazon Bedrock console, underneath Safeguards within the navigation pane, select Guardrails.
- Choose the guardrail you created and select Delete.
Alternatively, you need to use the SDK:
bedrock_client.delete_guardrail(guardrailIdentifier = "<your_guardrail_id>")
Key takeaways
Making use of guardrails is essential for sustaining accountable and protected content material era. With the ApplyGuardrail API from Amazon Bedrock, you may successfully average each inputs and outputs, defending your generative AI utility towards violations and sustaining compliance together with your content material insurance policies.
Key takeaways from this publish embrace:
- Perceive the significance of making use of guardrails in generative AI purposes to mitigate dangers and keep content material moderation requirements
- Use the
ApplyGuardrailAPI from Amazon Bedrock to validate inputs and outputs towards outlined insurance policies and guidelines - Implement chunking methods for long-context inputs and batching strategies for streaming outputs to effectively make the most of the
ApplyGuardrailAPI - Comply with finest practices, optimize efficiency, and constantly monitor and refine your guardrail implementation to take care of effectiveness and alignment with evolving content material moderation wants
Advantages
By incorporating the ApplyGuardrail API into your generative AI utility, you may unlock a number of advantages:
- Content material moderation at scale – The API means that you can average content material at scale, so your utility stays compliant with content material insurance policies and tips, even when coping with massive volumes of knowledge
- Customizable insurance policies – You may outline and customise content material moderation insurance policies tailor-made to your particular use case and necessities, ensuring your utility adheres to your group’s requirements and values
- Actual-time moderation – The API permits real-time content material moderation, permitting you to detect and mitigate potential violations as they happen, offering a protected and accountable person expertise
- Integration with any LLM –
ApplyGuardrailis an impartial API, so it may be built-in with any of your LLMs of selection, so you may make the most of the ability of generative AI whereas sustaining management over the content material being generated - Price-effective answer – With its pay-per-use pricing mannequin and environment friendly textual content unit-based billing, the API supplies an economical answer for content material moderation, particularly when coping with massive volumes of knowledge
Conclusion
By utilizing the ApplyGuardrail API from Amazon Bedrock and following the very best practices outlined on this publish, you can also make certain your generative AI utility stays protected, accountable, and compliant with content material moderation requirements, even with long-context inputs and streaming outputs.
To additional discover the capabilities of the ApplyGuardrail API and its integration together with your generative AI utility, take into account experimenting with the API utilizing the next assets:
- Consult with Guardrails for Amazon Bedrock for detailed info on the
ApplyGuardrailAPI, its utilization, and integration examples - Try the AWS samples GitHub repository for pattern code and reference architectures demonstrating the mixing of the
ApplyGuardrailAPI with varied generative AI purposes - Take part in AWS-hosted workshops and tutorials targeted on accountable AI and content material moderation, the place you may be taught from specialists and acquire hands-on expertise with the
ApplyGuardrailAPI
Sources
The next assets clarify each sensible and moral points of making use of Guardrails for Amazon Bedrock:
Concerning the Writer
 Talha Chattha is a Generative AI Specialist Options Architect at Amazon Internet Companies, based mostly in Stockholm. Talha helps set up practices to ease the trail to manufacturing for Gen AI workloads. Talha is an skilled in Amazon Bedrock and helps prospects throughout complete EMEA. He holds ardour about meta-agents, scalable on-demand inference, superior RAG options and price optimized immediate engineering with LLMs. When not shaping the way forward for AI, he explores the scenic European landscapes and scrumptious cuisines. Join with Talha at LinkedIn utilizing /in/talha-chattha/.
Talha Chattha is a Generative AI Specialist Options Architect at Amazon Internet Companies, based mostly in Stockholm. Talha helps set up practices to ease the trail to manufacturing for Gen AI workloads. Talha is an skilled in Amazon Bedrock and helps prospects throughout complete EMEA. He holds ardour about meta-agents, scalable on-demand inference, superior RAG options and price optimized immediate engineering with LLMs. When not shaping the way forward for AI, he explores the scenic European landscapes and scrumptious cuisines. Join with Talha at LinkedIn utilizing /in/talha-chattha/.